The security of the f-droid platform is based on pgp signatures yet not a signature verification app in sight anywhere. Hmmmm
If it is even possible to do signature verification in openkeychain (which I doubt) then it is an undocumented feature that 99.9% of android users have no idea how to use. That you would give that as an answer along with the fact trackers were found in the f-droid app casts serious doubt on the integrity of those running this platform imo.
Is that a FUD spreader I smell?
RTFM. In the app. Help, key confirmation tab.
I just re-read the openkeychain manual. There is no way to use that app to verify a file was really signed by f-droid so why are you lying?
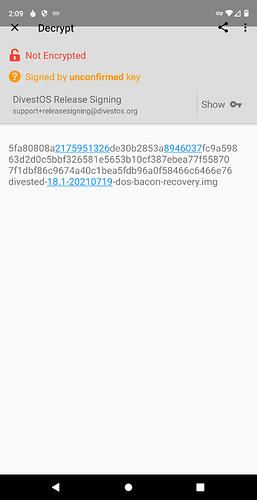
There is a ‘Decrypt/Verify’ function…
Decrypt/verify does not do that. It decrypts an encrypted file.
I assure you that it can indeed verify file signatures.
- First ensure you have the key for the signature
- Open from tab: Decrypt/Verify
- Select input file
“Signed by […] key”
-
Install Termux and
termux-setup-storage -
apt-get update && apt full-upgrade -y -
apt install gnupg -
apt install wget -
cd /sdcard/Download/ -
wget FILE-LINK -
wget SIGNATURE-LINKgpg --verify SIGNATURE-FILE.apk.asc FILE.apk
that’s it.
If you haven’t already imported the key, as with fresh install of Termux, you need to do
gpg --keyserver keyserver.ubuntu.com --search-keys admin@f-droid.org
before the gpg --verify.
@skewedzepplin if you think that is verifying file signatures do it to the f-droid app and show me where it proved the apk file was signed with the f-droid signing key.
@F-DD well that is my point exactly. We have people here that are encouraging users to bypass their own device security by sideloading apps that are downloaded from these unknown servers and they are not even providing a decent method of ensuring those files are at least compiled by them? Not even so much as a checksum? When you have to install a linux terminal and use command line instructions just to check if the apk file really came from them, there is something inherently suspicious about the entire thing. It says they do not care one iota about the users at all so what is their motivation for doing it? What was that? Did I hear three later agency?
![]()
I can say, just install CalyxOS or DivestOS which comes pre-installed with F-Droid, but then how do you verify the OS download?
I can say, just install OpenKeychain or Termux/gnupg first, but then how do you verify that app download?
I can say just trust HTTPS, but how do you trust the included certificates?
How can you trust your browser to not manipulate the file?
How can you trust your OS to not manipulate the file and verification results from other programs?
How can you trust your CPU to not manipulate your OS/programs?
At some point you inherently have to give-in and trust someone/something.
Verifying a root of trust of anything is long standing problem. You are welcome to come up with a new proposal.
I don’t have an answer for you and I am not going to argue with you.
Off the top of my head, at the very least I would provide checksums of each app so the user can use online tools like this one Checksum Calculator Online - AppDevTools to check the integrity of apps especially the f-droid.apk file before they install it. I would then include in the f-droid app a dialogue that informs the user of the results of similar checks on each file downloaded by the f-droid app. Anyone could therefore compare what the f-droid app is telling them with the results from their own checksum calculators to ensure they can trust the app thereafter.
Anyone can easily checksum the f-droid apk for an md5 and a sha256 using that tool it took just a few seconds to calculate the ones below for the f-droid apk. That would be well enough for most people to establish that root of trust. This is nothing new. This is simple and straightforward stuff using principles that were established decades ago so why do the f-droid devs ignore that?
MD5:79b5ae70cb731e1f57c1672786fc7367
SHA256:49128b38ccf5cb2676435dba1c6143f78a4e33dcd8bbca91a529881c94528ab5
You’ll trust a proprietary script on a webpage that loads helpers and
trackers from Google, but you have the gall to call F-Droid
compromised by governments…
I cannot comprehend.
What? Are you seriously telling me it does not occur to you how easily the accuracy of such a script can be verified by comparing its results to other similar web resources and offline apps? As f0or that particular one it was just an example.
$ gpg --verify org.fdroid.fdroid_1013050.apk.asc org.fdroid.fdroid_1013050.apk
gpg: Signature made Fri 09 Jul 2021 12:08:47 PM EDT
gpg: using RSA key 802A9799016112346E1FEFF47A029E54DD5DCE7A
gpg: Good signature from "F-Droid <admin@f-droid.org>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 37D2 C987 89D8 3119 4839 4E3E 41E7 044E 1DBA 2E89
Subkey fingerprint: 802A 9799 0161 1234 6E1F EFF4 7A02 9E54 DD5D CE7A
Seems OK, but would seem better if “trusted” after confirming ownership and trusts over beers in a pub…
OTOH,
$ apksigner verify --verbose org.fdroid.fdroid_1013050.apk
Verified using v1 scheme (JAR signing): true
Verified using v2 scheme (APK Signature Scheme v2): true
Verified using v3 scheme (APK Signature Scheme v3): true
Number of signers: 1
WARNING: META-INF/androidx.activity_activity.version not protected by signature. Unauthorized modifications to this JAR entry will not be detected. Delete or move the entry outside of META-INF/.
WARNING: META-INF/androidx.annotation_annotation-experimental.version not protected by signature. Unauthorized modifications to this JAR entry will not be detected. Delete or move the entry outside of META-INF/.
WARNING: META-INF/androidx.appcompat_appcompat-resources.version not protected by signature. Unauthorized modifications to this JAR entry will not be detected. Delete or move the entry outside of META-INF/.
WARNING: META-INF/androidx.appcompat_appcompat.version not protected by signature. Unauthorized modifications to this JAR entry will not be detected. Delete or move the entry outside of META-INF/.
WARNING: META-INF/androidx.arch.core_core-runtime.version not protected by signature. Unauthorized modifications to this JAR entry will not be detected. Delete or move the entry outside of META-INF/.
<snip>
starts out good, but the many Warnings cause some concern. Can someone explain why the Warnings are OK?
PS. apksigner may be a g66gle tool, but maybe can be trusted because it also is available from Debian. ![]()
Compared to other APK sites, F-Droid has one of the best security systems.
Termux is a good app, The only downside is that it no longer supports Android 5 and 6.
You can also verify Termux with gnupg after installation, of course. Or with a computer or laptop before installation.
No it does not. The f-droid security model is total horse shit. There is no proper way for the public to verify the apps they download are legit and even those who know to install linux terminals and use the required command line instructions cannot even prove the f-droid signing key is even the f-droid sighning key and on top of that there is a whole bunch of warnings that the packages were not even properly signed to begin with and therefore modifications to them cannot be detected.
Come on
Keep arguing