Ok so in the hopes of actually helping with that, another round:
15.05’22 18:00 CEST, some interesting stuff to see this time.
“Dauer” column stands for “Duration”, so full request duration.
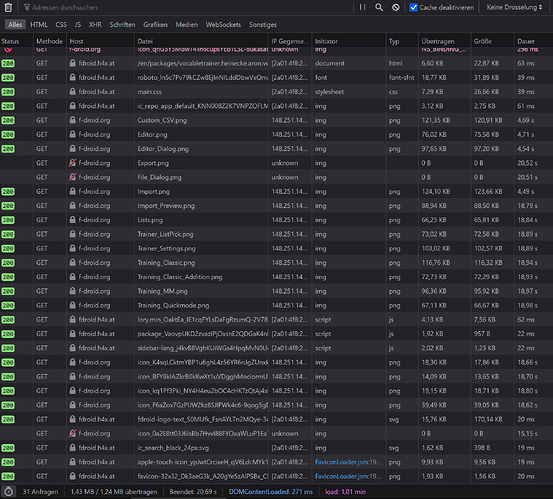
First the new solution h4x.at
https://fdroid.h4x.at/en/packages/vocabletrainer.heinecke.aron.vocabletrainer/
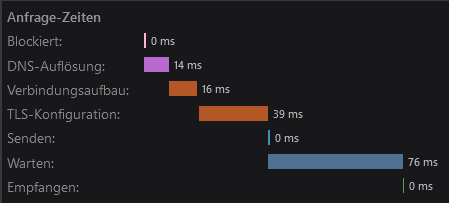
Disabled cache, first hit
Notably some of the fastlane images are served via http and not https and biggest part of them are served over f-droid, not h4x.at. Everything coming from h4x.at does get delivered very fast.
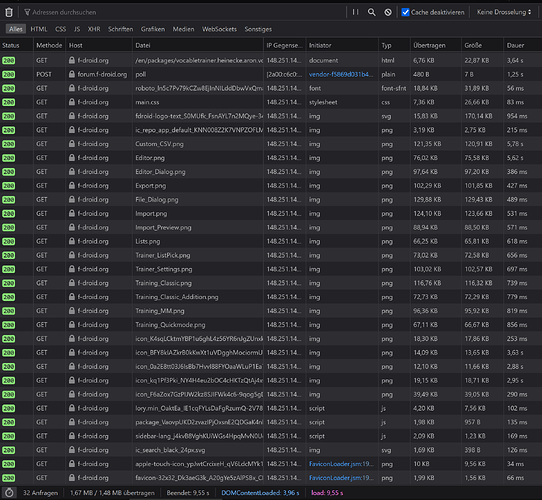
F-droid itself, for a baseline
https://f-droid.org/en/packages/vocabletrainer.heinecke.aron.vocabletrainer/
Disabled cache, first hit
As expected initial request takes 9 seconds, everything else varies a lot.
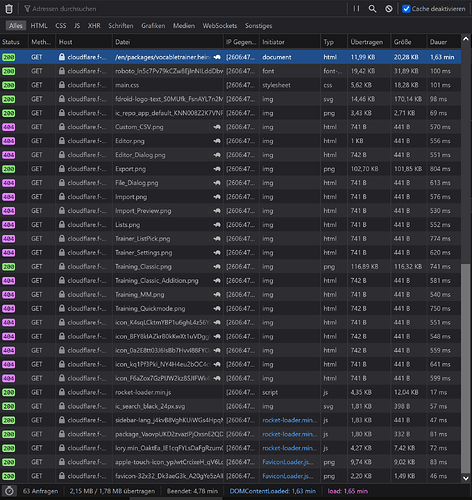
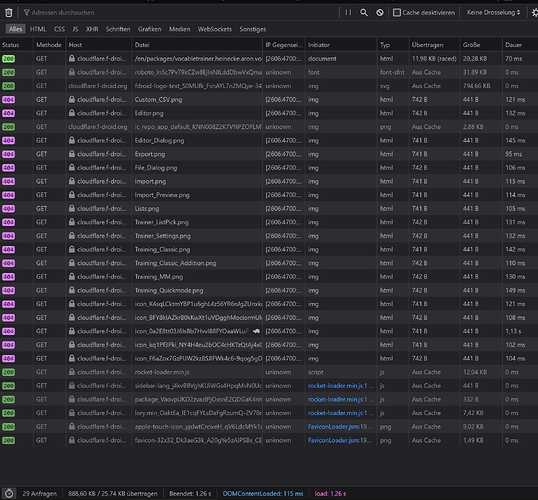
Now for cloud flare, where it’s getting interesting:
https://cloudflare.f-droid.org/en/packages/vocabletrainer.heinecke.aron.vocabletrainer/
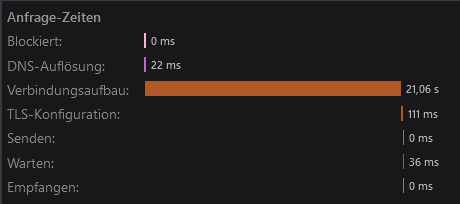
Disabled cache, first hit
1,6minutes for the first hit itself! (Certainly cold cache waiting for f-droid)
Nearly all fastlane images are 404, though not if you directly browse the URLs.
Example URL 404:
https://cloudflare.f-droid.org/repo/vocabletrainer.heinecke.aron.vocabletrainer/en-US/phoneScreenshots/Editor.png
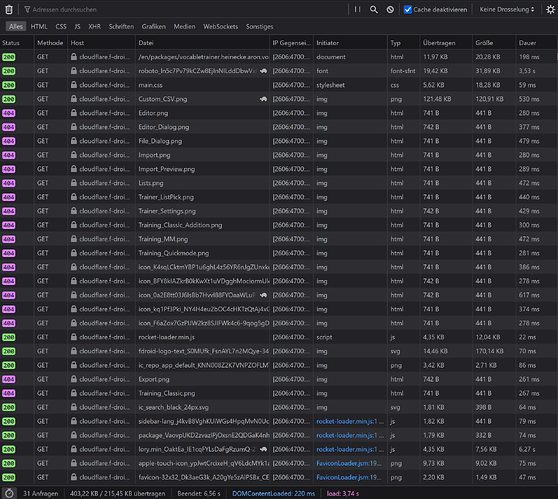
Let’s reload cloud flare to see the cache in effect
Disabled cache, second hit
https://cloudflare.f-droid.org/en/packages/vocabletrainer.heinecke.aron.vocabletrainer/
Stuff that doesn’t 404 is mostly fast. Some stuff seems to not get cached, marked by firefox with a turtle (and also the “Dauer” column).
And for completeness another cloudflare request, with caches.
https://cloudflare.f-droid.org/en/packages/vocabletrainer.heinecke.aron.vocabletrainer/