Sure, ill play! No worries, i build my own builds of GrapheneOS, and I am not as experienced or as knowledgeable in the deeper workings of it as @mbananasynergy, however I know a thing or two. I’ve been researching how it works on a deeper level than a standard user for about 6 months, and I can say that I have in that time, never seen Google Play Services, Store or Framework do anything at all, ever outside of their permission models!
Yes, I do believe that system apps need to be build into the system to be system level apps. They should be in /system/priv-app/
/system/ is a read only partition with 0 bytes available as well after it is built! Well, really after it is packaged… I can see all the system partitions being created as part of the app signing/factory build/OTA update creating process, which comes right after the build in the GrapheneOS build process It has been modified substantially from the standard Android build process, just like the Vanadium (GrapheneOS’s default Chromium based browser) has been, referencing standard AOSP code may not be 100% relevant to GrapheneOS!
I can say this with confidence because I’ve been building my own builds, and working my way through reading the GrapheneOS source code for about 7 months now! Modifying tiny bits of it, but so very cautiously, because it is very clean and well thought out code. The last thing I want to do is integrate a security flaw… More on this below, but first, I NEED to bring this up…
If you want to reference any code, or post screenshots, please reverence GrapheneOS code which is freely available.
Referencing regular AOSP code isn’t that relevant here… The GrapheneOS code is publicly available, so i dong know why your using other, not applicable code to attack the project… Probably because it sounds right to non technically-inclined users who don’t know any better, so in effect you are taking advantage of their lack of knowledge. Very shameful of you, *especially since you should know better!
You can also reverence it’s kernel code, but that’s mostly a GKI kernel with added hardening that can be integrated integrated into any Linux kernel (integrity mode/confidentiality mode, I believe GrapheneneOS uses Confidentiality mode, not 100% sure though… May only be enabled when Lockdown Mode is activated.)
Please STOP using the straw man of pretending to know what is happening inside of GrapheneOS by reading code that is not GrapheneOS code! When you put it simply like that, it does sound silly, doesn’t it? Also your using a formal logical fallacy, in and real debate (formal) it wouldn’t stand, but here it makes you sound like an expert, without needing to actually know anything about GrapheneOS! Lets base this on facts about the actual product you and I are talking about, OK?
Because i build my own flavor of GrapheneOS, I’m currently running a build where everything including the bootloader keys are signed by me, with my own signing keys. That enables me to sideload a temporary root without needing to unlock the bootloader.(locked bootloader root with fully working verified boot) so i can load apps temporarily like App Manager with full root, UID 0 permissions and inspect on a running production build of GrapheneOS, the claims you are making. The last post I made,
I got the information this way too.
I also use App Ops extensively on rooted and unrooted production builds of GrapheneOS. The 3 main Google apps in discussion here (Services, Store, Framework) start with NO permissions except network, and in App Ops (the backend to all permissions on modern Android systems) they are all “undefined.” On a system of root app they start with all requested permissions as “granted.”
I can see, and EVERYONE can see the permissions Google Play Services wants access to by going to it’s app settings screen, then Permissions, then the three dots in the upper right corner and selecting “All Permissions.” These are not all currently granted permissions, unless it is a system or root level app on the stock Google OS!
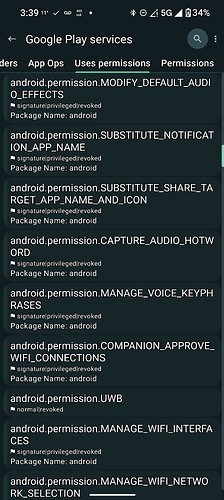
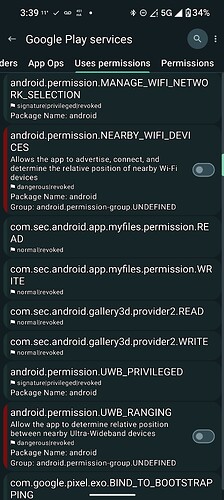
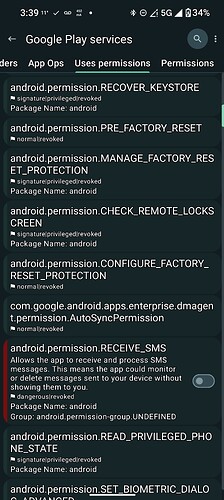
I can see a massive amount of permissions there for Google Play Services, and even more in App Manager as it exposes the highly privileged, system level permissions! It also says that almost all of them are “revoked”! If it were a system app, then they would be GRANTED!
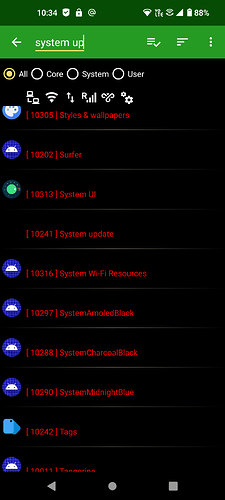
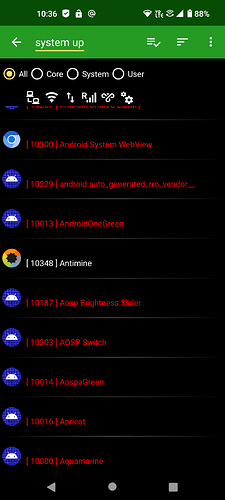
Here are sone of the MANY permissions for Sandboxed Google Play Services, that it requests from the system, there are really enough for over 30 screenshots, so here is a few off the top:
Notice they are all “revoked”? Wouldn’t be possible if it was a system level app!
Didn’t you start all this off by claiming that these apps must have UID’s of 1000 or 0? And that cannot be changed, therefore because of some code that is not GrapheneOS code, but standard AOSP code, they must have full system level privileges?
Now your shifting tactics after I pointed our that on GrapheneOS they do not have UID’s of 1000 or 0! Shows that your arguments aren’t on solid ground if you need to change them, and you seem insecure if you cannot even concede the point when faced with proof that you were wrong…
Anyways, on to more proof!
Also if it were a system app, a user **Would not be able to revoke permissions from it without becoming a higher privilege level themselves, something forbidden in the Google stock OS, and on standard builds of GrapheneOS! Again, I only can do this because i have built multiple kernels with root integrated into one of them, and i switch modes by sideloading different OTA updates.
I’ll post again my observations of the **different SElinux rules for system apps with privileged permissions, vs the Sandboxed Google Play Apps, and then a regular, user installed app:
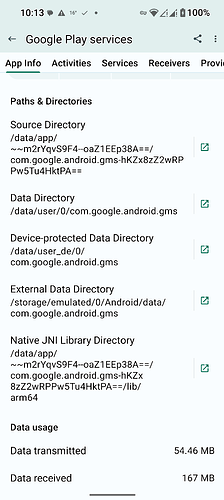
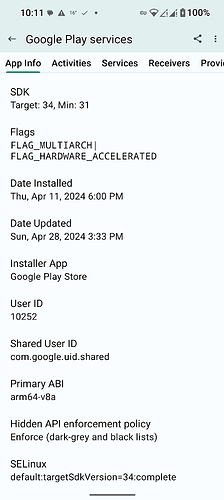
Google Play Services SElinux Policy (and installed/data directories):
default:targetSdkVersion=34:complete
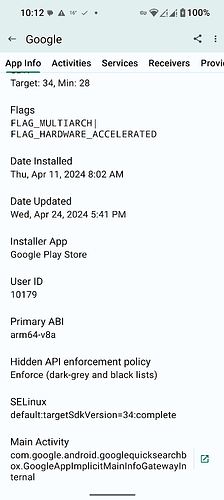
Google app for running Gemini on GrapheneOS SElinux policy:
default:targetSdkVersion=34:complete
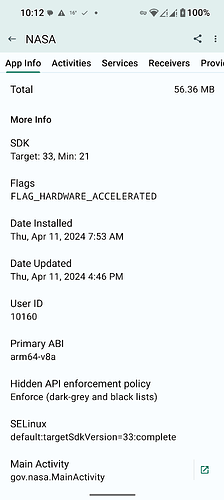
Another random user app (NASA) SElinux policy:
default:targetSdkVersion=33:complete
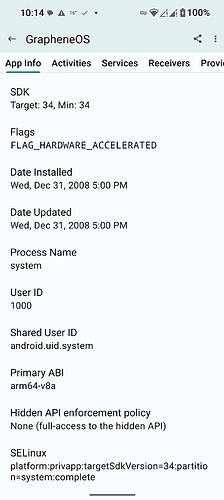
Main system app bundle SElinux policy (and installed/data directories):
platform:privapp:targetSdkVersion=34:partition=system:complete
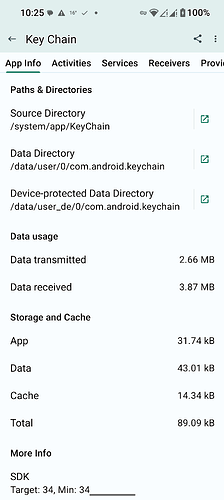
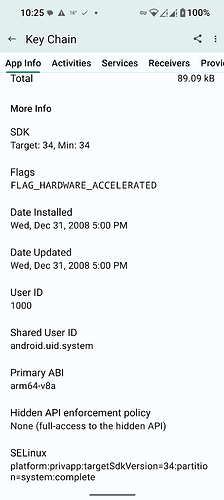
Android Keychain non-user facing system app SElinux policy/installed/data directories:
platform:privapp:targetSdkVersion=34:partition=system:complete
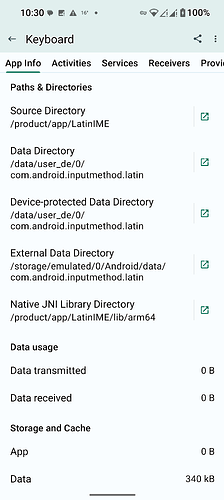
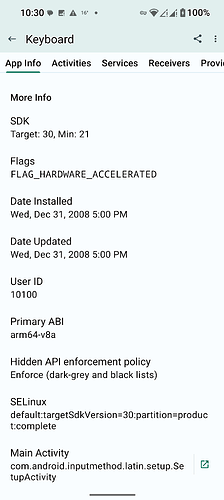
Non-privileged system-level app (default AOSP keyboard) SElinux policy:
default:targetSdkVersion=30:partition=product:complete
Default AOSP Phone dialer SElinux policy:
default:privapp:targetSdkVersion=30:partition=product:complete
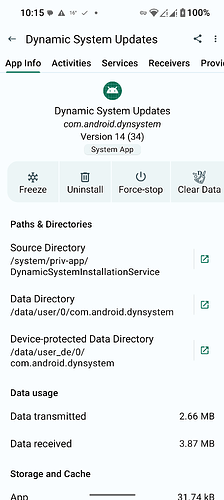
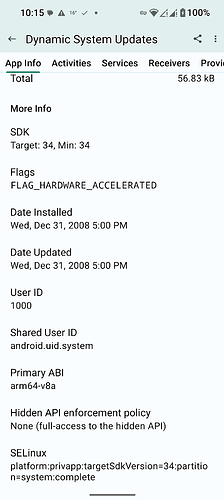
Dynamic System Updates system app SElinux policy/install/data directories:
platform:privapp:targetSdkVersion=34:partition=system:complete
The apps that are marked as “privapp” cannot be disabled. The system apps that are simply partitioned on read only filesystem’s outside of user control you can disable.
So… I think you can easily see that the system apps have different permissions based on SElinux on GrapheneOS. SElinux is used heavily on GraphebeOS because it is such a powerful tool, used of many desktop operating systems to lock down application’s permissions very effectively! It is much stronger than the simple permission model that most users are aware of.
You can also see, both system level apps that are not privileged, as well as user apps are installed with UID’s of 10xxx. This just goes to show (in multiple ways) that Google Play Services and the other two Google apps that make up Sandboxed Google Play are not system apps and do not hold system level permissions!
I have now shown you that they:
-
Do not reside where system APKs reside, because they are not built into the operating system but optionally added later.
-
They do not have a UID label of a privileged app, nor are they located where privileged apps are on the correct partition for them.
-
The SElinux policy for these Sandboxed Google apps is that of unprivileged user apps. They don’t even have an SElinux policy of unprivileged system apps, giving them system-level partitioning different from user apps, **the policy for them is identical to that of regular user apps!
-
Finally, I have shown you that Google Play Services may request all of the powerful, system permissions that it is used to getting, but receives almost none! If it were a system or root level app with special access, it would get these.
Convinced yet? Really I care little about convincing you, my ego doesn’t depend at all on what some random person on the internet thinks. This post and the effort that went into it is for all future viewers so they get a taste of the truth of things, and they aren’t taken in by the outright falsehoods backed by made-up data you are presenting.
The truth has a way of rising to the top, and when placed next to falsehood, people are usually quick yo recognise which is which…