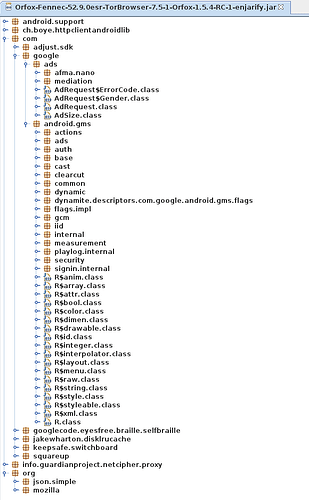
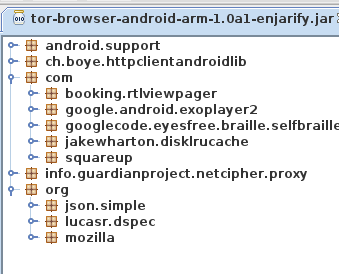
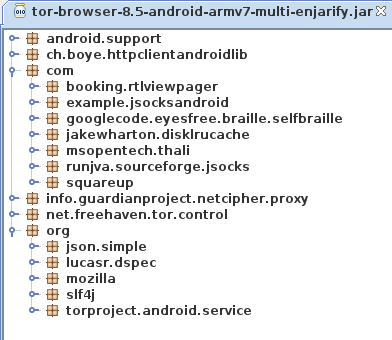
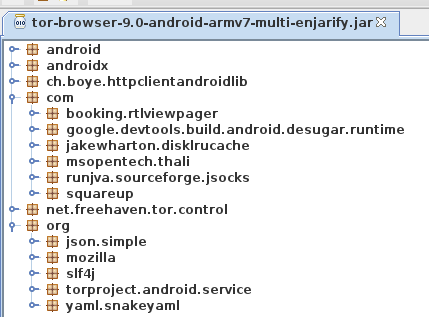
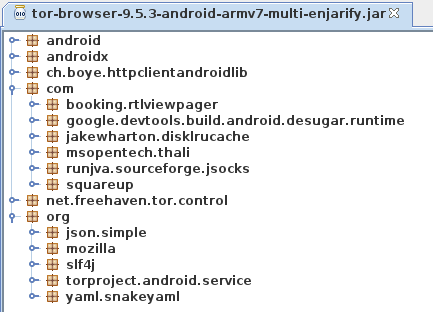
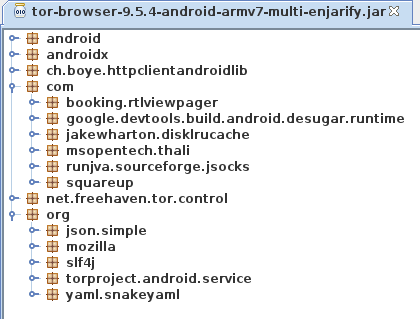
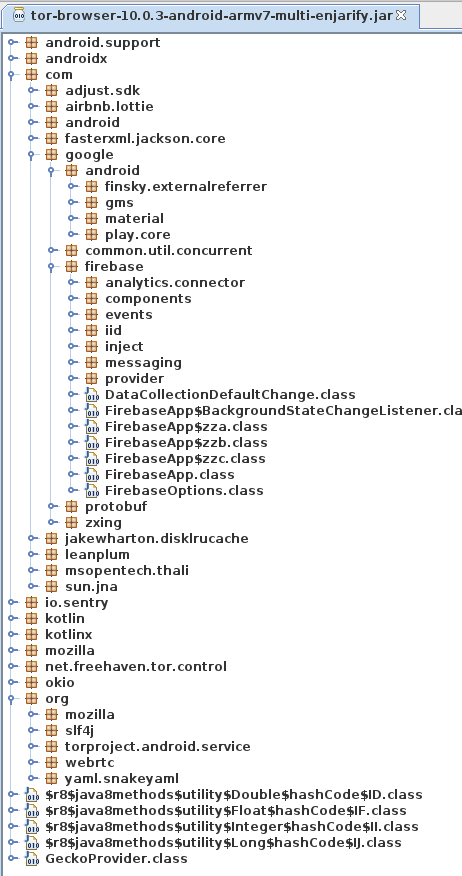
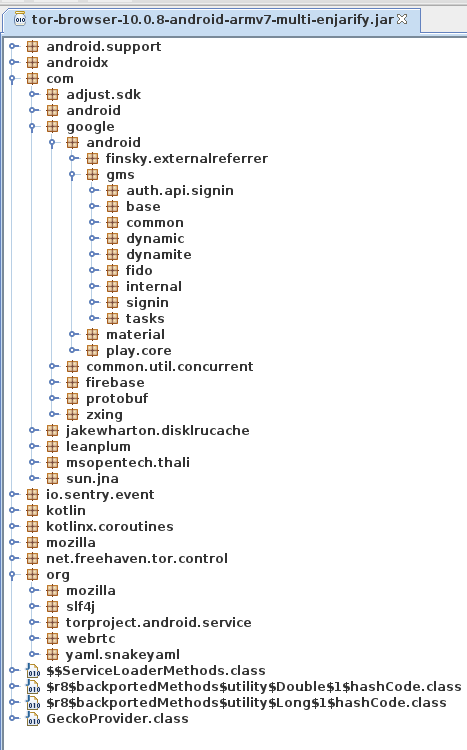
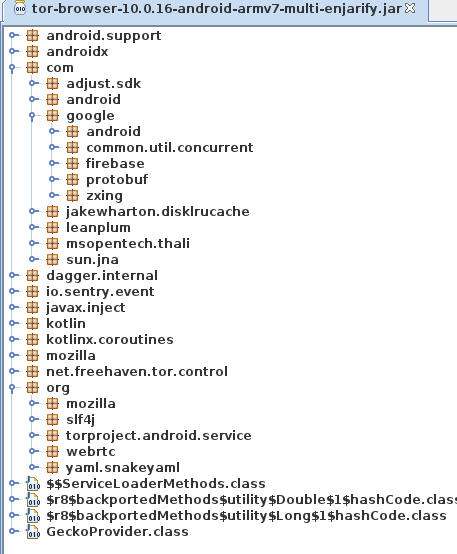
Looks like a Fennec build option was changed and that stuff was mistakenly
included in Tor Browser
This definitely appears to be a regression introduced during the Fenix rebase. From @relan’s work it is shown that there is no build option in Fenix to remove these, like there was in Fennec.
I had asked a while ago if there was going to be any collaboration, but it obviously seems not: Welcome a new Fennec F-Droid - #3 by SkewedZeppelin
Also of relevance last time this happened it took a while to work out: https://bugzilla.mozilla.org/show_bug.cgi?id=1419581