If someone compromised F-Droid server (and webpage) will change checksums too, you need to download “PGP Signature” which is attached to the apk, you need PGP software to verify the apk, and use the apk signature with the PGP public key from F-Droid, public keys are generated from a private key, only F-Droid has this private key, so if some malicious entity compromises the server, it shouldn’t able to replicate the public key (because is generated by a strong encryption algorithm)
This means, if the PGP signature attached to apk is compromised, it would not match the public key, that is published in keyservers.
-
GNU/Linux distribution: install gnupg from terminal, then search key for
admin@f-droid.organd import itgpg --search-keys admin@f-droid.org
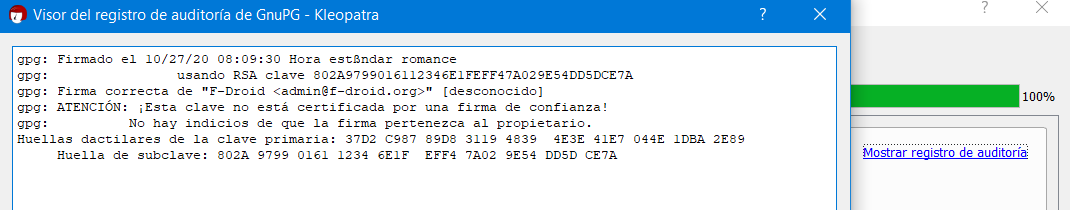
ID should be 41E7 044E 1DBA 2E89, primary fingerprint 37D2 C987 89D8 3119 4839 4E3E 41E7 044E 1DBA 2E89. (you can find subkey in the link you posted, also verify primary fingerprint)
Then,gpg --verify /path/to/file/F-Droid.apk.asc(APK should be in the same folder) after that, it should output “Good signature…” probably a warning because you didn’t certified the key, no problem if the fingerprint of the public key matches. -
Android: install Termux, then gnupg, same process.
Or install OpenKeyChain. -
Windows: install Gpg4win (Kleopatra is the GUI), process should be easier, just go ahead and search for F-Droid public key (search function inside the program) and import, then verify.
“Firma correcta” : Good signature.